Penetration Testing in Finance: A how-to Guide
17.07.2023
As the world continues to become more digitized, the financial industry is at a higher risk of cyber attacks than ever before. Financial institutions are particularly vulnerable targets for cybercriminals, due to the sensitive information they hold and the high value of their assets. According to a report by Accenture, financial services spend more than any other industry fighting cyber-attacks. What is more, in 2021 this cost them around $1.59 million to remediate just ransomware attacks alone.
In this how-to guide, we will explore the benefits of penetration testing in the Finance industry and provide practical advice for conducting successful testing. We will cover the various types of penetration testing, the steps involved in planning and executing a test, and how to interpret and act on the results.
Penetration testing overview
Penetration testing, also known as pen testing, is a security testing method that evaluates the security of an organization's IT infrastructure by simulating real-world attacks. Its goal is to identify vulnerabilities in the system that could be exploited by attackers and to provide recommendations for improving security. The importance of penetration testing in the Finance industry cannot be overstated. Companies in the sector are prime targets for cybercriminals due to the vast amount of sensitive data they hold. These attacks can be highly damaging to both the organization and its customers, and can result in the loss of funds, identity theft, and other financial crimes. Penetration testing is a critical component of a comprehensive cyber security strategy for financial institutions. By regularly testing their systems, companies can proactively identify and address vulnerabilities before they are exploited by attackers, helping to safeguard sensitive data and prevent costly security breaches.
Download whitepaper: Penetration testing for protecting financial institutions against cyber attacks
Аs a provider of cyber security services, Accedia understands the critical role that penetration testing plays in identifying vulnerabilities and weaknesses in our clients' systems. Based on our experience working with companies in the financial sector, we are going to share with you some valuable tips and steps you can follow to ensure the security of your data.
Understanding the cyber security risks for financial institutions
Financial institutions face a range of cyber security threats that can cause significant harm to their operations, reputation, and customers. Some of the most common threats include:
- Phishing Attacks: Fraudulent attempts to obtain sensitive information such as login credentials, credit card details, and other personal information by posing as a trustworthy entity. These attacks can be conducted via email, social media, or text messages.
- Distributed Denial-of-service (DDoS) Attacks: Include overwhelming a network or website with traffic from multiple sources, causing it to become unavailable to legitimate users. They can be used to extort money, disrupt business operations, or distract from other attacks. At the beginning of 2023, we saw a 6% quarterly increase in large-scale volumetric DDoS attacks, which refers to attacks exceeding 100 Gbps. Among them, DNS-based attacks emerged as the most commonly used vector.
- Ransomware Attacks: Involve malware that encrypts data on the victim's computer or network, and then demands a ransom in exchange for the decryption key. These attacks can result in the loss of important data and disrupt business operations. According to a report, in Q1 2023 a weekly ransomware attack was encountered by 1 out of every 31 organizations globally.
- Social Engineering Attacks: Being the most common type of cyber-attack in 2022, social engineering manipulates individuals into divulging sensitive information or performing actions that compromise security. Examples include impersonating a trusted employee, using pretexts to gain access to sensitive information, or baiting users into clicking on malicious links.
A cyber-attack on a financial institution can have severe consequences, including:
- Financial loss – Can occur in the form of theft of funds, business interruption, or damage to IT infrastructure.
- Reputational damage – Can be crucial as customers may lose faith in the institution's ability to protect their sensitive information, leading to a loss of market share and revenue.
- Legal and regulatory repercussions - May result from a breach of privacy laws or regulations, leading to potential fines and lawsuits.
- Loss of customer trust - Can be difficult to regain and may have long-term impacts on the institution's bottom line.
Cyber security threats to look out for in 2024
Planning and preparing for a penetration test
Before conducting a penetration test, financial institutions should take several important steps to ensure the success and legality of the process.
- Define your scope and budget by prioritizing high and low-priority areas that require testing. Identify areas of vulnerability, such as operating systems, application code, and configuration files. For low-priority areas, focus on internal business operations.
- Include financial and customer data sources in your comprehensive penetration testing plan. Test both the data sources and the software that connects to them and their supporting infrastructure. This is especially important in financial services because of data sensitivity.
- Consider penetration testing remotely accessible resources, such as remote employees, building automation systems (BAS), and other remote endpoints. Test these endpoints to identify your exposure to external attacks and assess your publicly accessible assets.
- Follow a penetration testing methodology that aligns with your objectives. Choose a methodology that matches your needs, such as the Penetration Testing Execution Standard (PTES), Payment Card Industry Data Security Standard (PCI-DSS), or Open-Source Security Testing Methodology Manual (OSSTMM).
- Prepare by knowing what you need to test and how you’ll conduct it. Seek proper authorizations from your hosting or cloud provider, identify team members who will review the test report and fix issues, and schedule patching to occur after the testing is completed.
- Create a communication plan to ensure a smooth process. Establish communication protocols between you, your team, and the penetration testing provider, and conduct regular meetings to monitor progress and exchange essential information.
- Choose a qualified penetration testing service provider who uses automated and manual techniques to uncover vulnerabilities and advanced threats in your environment. Ensure that the provider examines both internal and external IT assets and generates custom reports that highlight the risks of identified and exploited vulnerabilities.
Cloud security: Protecting your data, applications, and infrastructure
Choosing a penetration Testing service provider
A penetration testing service provider will simulate a real-world cyber-attack on your systems and infrastructure to identify weaknesses that attackers could exploit to gain unauthorized access to your data or systems. They will then provide you with a comprehensive report of their findings and recommend remedial actions to improve your security posture.
By working with a reputable and experienced penetration testing service provider, you can ensure that your organization is better protected against cyber threats. This is especially important if you handle sensitive data or operate in regulated industries, where data breaches can result in severe financial, legal, and reputational consequences.
There are four main steps you can follow to find the right penetration testing service provider:
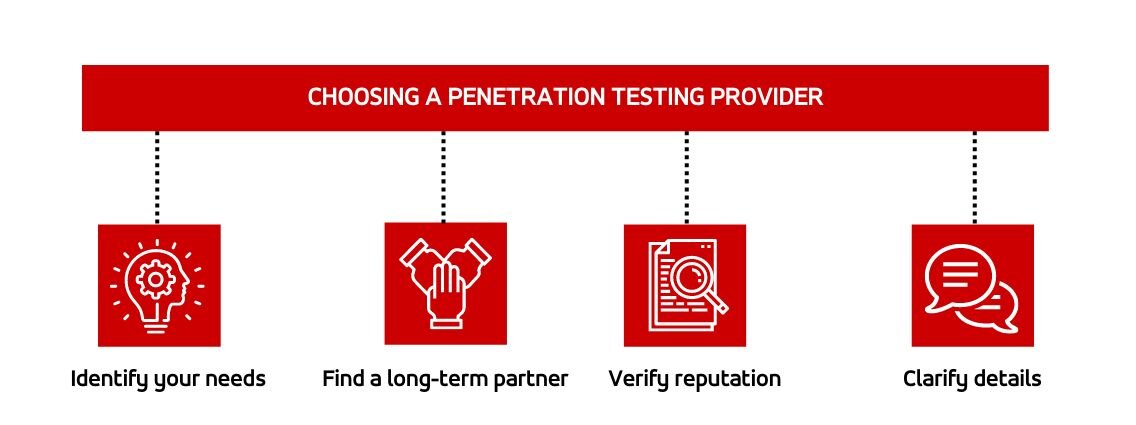
- Identify your needs - Have a clear understanding of your requirements, including your testing needs, budget, and goals. Don't treat penetration testing as a tick-box exercise. Be wary of providers offering unrealistic prices and turnaround times. Also note that some offer substandard "penetration testing" which is nothing more than an elaborate vulnerability scan, which is why they can charge less.
- Find a high-quality long-term partner - Begin the procurement process by searching for a service provider with whom you can establish a long-term relationship. Penetration tests should be conducted frequently, so it's essential to find a team that you trust. Seek out partners who have the necessary expertise to cover all of your requirements and guide you on which tests will best suit your objectives. Additionally, keep in mind that the very same partner can help your overall security. So, make sure to thoroughly research their entire service portfolio and take full advantage of their knowledge and expertise.
- Verify Credentials and Reputation - It is recommended that you only work with a company that has reputable external accreditations. You should research potential service providers to determine their reputation and experience, such as client testimonials and reviews, reports, thought leadership, and more.
- Confirm Details and Engage - After identifying one or more potential service providers, engage with them to determine whether they are the right fit for you. Before finalizing your selection, ask questions to clarify details, such as the provider's penetration testing methodology and how they will tailor their approach to your specific objectives and issues. Request to see a sample report and inquire about post-testing remediation guidance and any available free retests.
Accedia penetration test success story
Accedia has carried out numerous cyber security assessments and penetration tests for various clients in the finance industry. A recent project included the evaluation of the security weaknesses of a developed application using technologies including SQLMap, ZAP, Nmap, dirsearch, Nikto, Metasploit framework, Burp Suite, and Kali Linux. Our team carried out a penetration test to uncover any issues that could potentially jeopardize the solution's confidentiality, integrity, or availability. The discovered vulnerabilities could allow a potential attacker to:
- Access sensitive information they were not authorized to view.
- Compromise accounts and passwords through automated guessing script attacks.
- Further analysis also showed that sensitive production database access credentials are stored in plain text format as part of the project source code pack.
During the testing our team didn’t uncover any critical vulnerabilities, however, there were a few medium ones such as:
- Logout didn’t invalidate the JWT token.
- Account enumeration attack vulnerability.
- JWT Signature not verified on frontend loading.
In conclusion
Penetration testing in the Finance industry plays a crucial role in the cybersecurity strategy of organizations, given the escalating risk of cyber attacks and the potential consequences they can have on financial institutions. By conducting regular penetration tests, organizations can proactively identify vulnerabilities, address them promptly, and protect sensitive data from exploitation. When choosing a penetration testing service provider, it is essential to consider their credentials, reputation, and ability to deliver comprehensive and tailored assessments. Ultimately, investing in penetration testing in the Finance industry can help companies mitigate risks, maintain customer trust, and safeguard their operations and reputation in an increasingly digitized world.
Want to access our complete guide on conducting penetration testing in Finance, some of its most popular techniques, and much more? Download your free whitepaper now!