How DevSecOps can transform application development
14.04.2022
The importance of IT security is nothing new, however, teams still rarely implement it correctly, timely, or efficiently. And even though introducing DevOps was a big step in the optimization of the software development process, up until recently security has been overlooked by many organizations. To change that and turn the development of safe and secure application into a priority we see a huge rise in the adoption of DevSecOps.
In this article, we’ll talk about what are the benefits of DevSecOps and how your organization can not only implement the framework but also make it a game-changer for your business. We’ll see why 2022 is predicted to be the year of DevSecOps and how you can take advantage of it.
What is DevSecOps?
According to a ThycoticCentrify report from 2021, 57% of organizations suffered security incidents related to exposed secrets in DevOps. In a standard software development lifecycle, the norm has always been to leave security for last. Managed by a separate security team, it was a process separated from the development itself. However, this, made the remediation of potential issues much slower and more complicated, creating an unplanned bottleneck for the entire project. To fix that, many organizations are now adopting DevSecOps as a framework.
The goal of DevSecOps is to blend together all phases of the development lifecycle. Its goal is to integrate security all the way through the design, deployment, testing, and delivery. This goes hand in hand with the shared responsibility all teams carry for the implementation of the best security practices and tools. It’s no surprise that DevSecOps’ motto is “software, safer, sooner”. This is a perfect illustration of what DevSecOps stands for - the ability to detect and manage any security threats earlier when they still haven’t done any harm to the software application. As a result, it saves time and money on taking care of it before it’s too late.
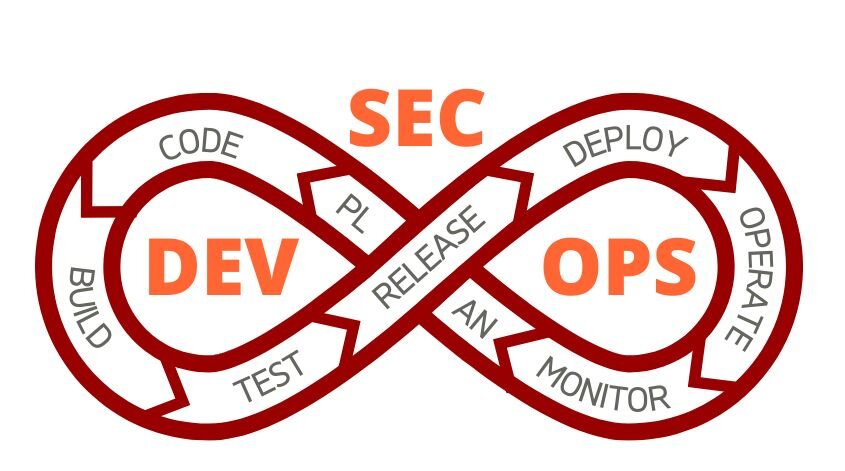
2022 is predicted to be the year for DevSecOps as security becomes one of the most important aspects of DevOps for developers. As Johnathan Hunt, VP of Security, GitLab said: “We will see a big jump in the adoption of DevSecOps in 2022 as more and more companies need to shore up their defenses against outside attacks.” Those threats such as fraud and code leaks are just getting more and more dangerous and unpredictable. Thus, companies from all industries are rightfully so looking for ways to quickly overcome the challenges of successfully implementing DevSecOps. Specifically, they may include finding the proper tools to integrate into the DevOps workflow, educating and training all teams, and much more.
Why do you need DevSecOps?
The adoption of the DevSecOps framework can have a massive impact on organizations. It can help them be more agile and quickly adapt to innovation while making sure security goals and principles are met. Take a look at some of the main benefits DevSecOps can bring to your business.
Faster security
In the past years, DevOps has allowed 60% of developers to release code twice as fast. This, however, can often be at the expense of security testing. 42% of participants in the same survey are confident that it happens way too late in the development lifecycle. Consequently, this makes threats and errors hard to figure out and thus fix on time. DevSecOps helps fix those problems by using tools and platforms to gain visibility into code and security gaps, development issues, and more. By merging together development, compliance, and security, DevSecOps allows teams to move to deployment much faster without risking the integrity of the code, the final solution, and naturally, the satisfaction of the end-user. With the latest trends in 2022, we are only expecting that process to become even faster and more secure than ever.
Automated security and testing
The adoption of DevSecOps allows automation of all compliance tests while providing logs and documentation. As a result, this offers transparency and traceability by creating audit trails. Automated reports can present the level of threat of each discovered issue. This helps development and security teams prioritize and plan their work and immediately address any critical vulnerabilities. Merging security into all phases of the development lifecycle can sometimes cause confusion as to who is responsible for what. Automation takes that confusion out of the way by presenting the team in charge with remediation options directly when a threat has been discovered.
Better scalability
Scalability is one of the main priorities when adopting DevSecOps. Companies that manage to use the right tools, implement automated checks, educate their teams, and define workflows, are well-prepared to meet any challenges or needs that may come up in the future. Once a faster delivery of features and products is achieved, organizations are on the right path to making scalability their priority. This also allows to create more thorough documentation, use cutting-edge technologies, cloud infrastructures, and much more.
Lower risk of unplanned spending
The automation behind DevSecOps allows speeding up time-to-market by implementing security checks and assessments throughout the entire development lifecycle. This is a very important factor when trying to beat the competition and meet the client’s requirements and expectations. On the other hand, DevSecOps helps detect any issues without the need of a human factor – thus making the processes more cost-effective and again – mitigating possible delays and fees related to them. Another way of limiting unplanned spending by implementing DevSecOps is detecting threats in advance, which can otherwise result in millions of dollars lost.
A good example of that is the ransomware cyberattack that Colonial Pipeline suffered in 2021. The organization had to halt all pipeline operations to contain the attack and paid the hackers around $4.4 million to restore the system.
Best DevSecOps practices in 2022
Shift left
In 2021 70% of security teams have reportedly shifted left according to GitLab's DevSecOps 2021 Survey results. This is a huge change from what we have witnessed in the earlier years when security assessments were performed as the software was ready to be deployed. This, of course, hid many potential rollout delays and unexpected costs. Here comes the idea of shifting security practices to the left. Meaning integrating security as early as possible into the software development lifecycle. This also includes changing the entire culture and mindset of all involved teams and embracing the security-centric sentiment.
Educate teams and start with the leadership
As with the adoption of any new concept and mindset shift, the overall embrace of DevSecOps should start from the leadership. They are the people who should first and foremost understand the benefits of DevSecOps. They should guide this change and swift everyone away from the outdated perception of security and development. To do so transparency and open communication are essential. Make sure everyone understands why the adoption of DevSecOps is essential for the well-being of the entire organization and how they can be a vital part of it. Set goals, define challenges, and prioritize. Above all, make sure all teams are educated on the topics of DevSecOps. Ultimately, this will allow developers to better understand security requirements, think critically, and create a software product taking into consideration security from the very beginning.
Master the right DevSecOps tools
In order for DevSecOps teams to be quick and efficient in what they do, they require the right set of application security tools to help the automation of processes as much as possible. Many vendors do offer a comprehensive suite of tools such as dynamic and interactive analysis testing (DAST and IAST), static application security testing (SAST), and software composition analysis (SCA). Additionally, more tools included in the DevSecOps realm are Log Analysis, Container Security, Penetration Testing, and Web Application Firewall (WAF). However, in order for teams to execute security checks and fixes as thoroughly as possible, the data provided by those tools needs to be further de-duplicated. Only then teams can create a single set of results, and decide which issues are critical and which they can deprioritize for the time being.
How digital transformation enables data analytics in finance?
Bet on infrastructure as code
Infrastructure as Code (IaC) is a strategy that codifies and manages IT infrastructure as software. Its benefit is that operations and developers teams can avoid manual processes such as installing and configuring hardware devices. Instead, IaC allows to automatically monitor, provision, and manage resources via software. However, IaC is much more than just automation. It offers continuity by automatically provisioning and configuring all environments eliminating the risk of human error. Additionally, IaC provides traceability, improved efficiency throughout the software development lifecycle, and consistency in the delivered configurations. It also helps teams easily apply and test security updates.
Embrace the shared responsibility model
When an organization moves from in-house storage to the cloud, security and compliance are no longer the duty of a single entity. Rather, all parties – the cloud service provider and the customer company, share responsibility for different architecture components. If we need to break it down – the cloud provider is in charge of the security of the cloud. This includes hardware, software, facilities running the cloud, and more. While the customer – for all cloud configurations and data such as access policies, network security, access, authentication, and more. Thus, organizations should perform thorough research regarding which components are governed by them and which by the cloud provider. This helps eliminate the risk of leaving any part in limbo. Afterward, create a list with all unattended components and map them out finding tools and services ensuring their proper security.
But to begin with - define your overall security strategy
To identify your security strategy, goals, and next steps, there are some things you need to take into consideration. Even though some may seem rather obvious make sure you create a clear checklist when implementing DevSecOps. Some of these steps can include:
- Know when and how updates will happen
- Define the security escalation process
- Perform constant security monitoring
- Always test the code before deployment
Of course, depending on your case, the implementation of DevSecOps can include other specific operations. Thus, it’s crucial to perform proper research and plan your strategy well.
Conclusion
Today, the rapid and continuous adoption of cloud platforms and shared resources has made software development even more dynamic, fast, and frequent, allowing iterations to take weeks or sometimes even days. This is all possible thanks to DevOps. As a natural step forward, in the last few years, we have seen the rise of DevSecOps. It helps minimize the vulnerabilities that reach production, betters security, creates scalability, and increases transparency and collaboration between teams. Additionally, it manages to reduce human error and costs, and ultimately speed up time-to-market. Finally, DevSecOps helps solutions be more secure and reach the end user much faster while doing that using fewer resources.
Make sure to learn more about our DevOps services and reach out if you have any questions.
Note: This piece is written in collaboration with Ivan Iliev - DevOps Consultant at Accedia with extensive experience in cloud administration and automation. In his work at Accedia he has helped multimillion companies build modern IT infrastructures and deliver cloud-native solutions.